Lately, experts have found a number of weaknesses linked to DNS in widely used TCP/IP stacks. DNS is like a phone book for the internet, it helps your computer find where to go. The specific weaknesses found are still being studied, but they could potentially affect a large number of devices connected to the internet. We don’t have an exact number yet, but it’s likely in the millions.
Definition of DNS
The Internet, one of the most impressive inventions of mankind, is actually quite straightforward compared to other modern technologies like CPUs, microcontrollers, and FPGAs. At its core, the Internet is just a platform that lets any two devices connected to it share information. You can think of the connection between these two devices like a serial port. Data is sent over this connection in the form of bytes, and it’s up to the devices to make sense of these bytes.
For one computer to communicate with another, it needs to know where the other computer is, much like how you need to know the address of a house to visit it. Each device connected to the Internet has a unique address called an IP address, which is a series of numbers.
Because devices are constantly connecting and disconnecting from the Internet, Internet service providers have to recycle old addresses. Otherwise, we’d run out of address numbers too quickly. This is known as a dynamic IP address, and it means that a device gets a new IP address each time it connects to the Internet.
This can cause issues when computers and servers are hosting websites. By the time everyone learns the IP address of the computer they want to connect to, that number has probably changed. Plus, numbers aren’t very user-friendly. That’s where the DNS comes in.
A Domain Name Server, or DNS, is a special server that keeps a list of website names and their IP addresses. When a computer wants to connect to a specific website, it first contacts the DNS (whose IP doesn’t change). The DNS then tells the computer the IP address of the website it wants to connect to. With the correct IP address in hand, the computer can continue with its connection.
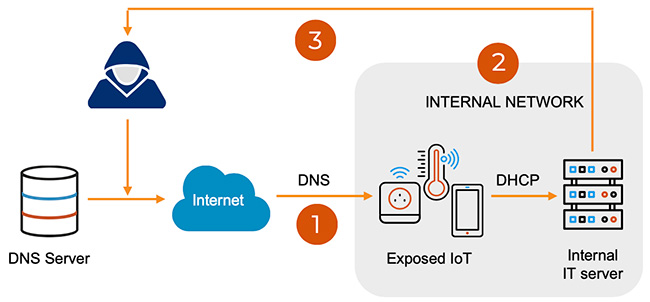
DNS Weaknesses Discovered Impacting IoT Devices
Recently, a group of researchers from a company called Forescout discovered nine security weaknesses, all grouped under the name NAME:WRECK. These weaknesses impact various TCP/IP stacks, which are used by IoT devices to communicate on the internet. A TCP/IP stack is like a device’s communication manager, handling tasks like sending and receiving messages, asking for names from DNS servers, and managing protocols like HTTP.
The researchers found that these weaknesses exist in the way multiple TCP/IP stacks, used in different IoT devices, interact with DNS servers or implement DNS. These vulnerabilities can make IoT devices susceptible to Denial of Service attacks, which can essentially freeze a device’s internet connection. They can also be exploited through Remote Code Execution, which allows an attacker to inject and execute any code they want on the device, effectively taking full control.
These vulnerabilities are usually the result of poor implementation of a standard, rather than a fault in the standard itself. A well-known example of this is the Heartbleed vulnerability in OpenSSL, where the developers didn’t properly check the boundaries of buffers, allowing them to be easily overflowed and access protected memory areas.
Forescout has identified three major TCP/IP stacks that are affected: Nucleus NET, FreeBSD, and Netx. However, this doesn’t mean that stacks developed by others are necessarily safe, and they could also be affected. While patches have been released for all three of these stacks, systems running older versions may still be vulnerable. As a result, Forescout is encouraging engineers to check the devices they’ve deployed for any vulnerabilities.
What is the number of impacted devices?
It’s really hard to figure out exactly how many devices are at risk because there are so many IoT devices out there (over 20 billion). But the folks at Forescout have made an educated guess for what they think is the least bad scenario, and even then, the numbers aren’t good. They estimated that if just 1% of the 10 billion devices that use the three TCP/IP stacks mentioned earlier are vulnerable, that would mean 100 million devices are at risk.
This becomes an even bigger worry when you consider that many government institutions use systems like FreeBSD. If hackers were able to exploit the TCP/IP stacks and use remote code execution to get into protected areas, data privacy could be seriously compromised.
The IoT world has made it possible to quickly roll out AI and other advanced technologies. But unless these devices can be easily fixed and updated, they could make the world a more vulnerable place.
Read more:

